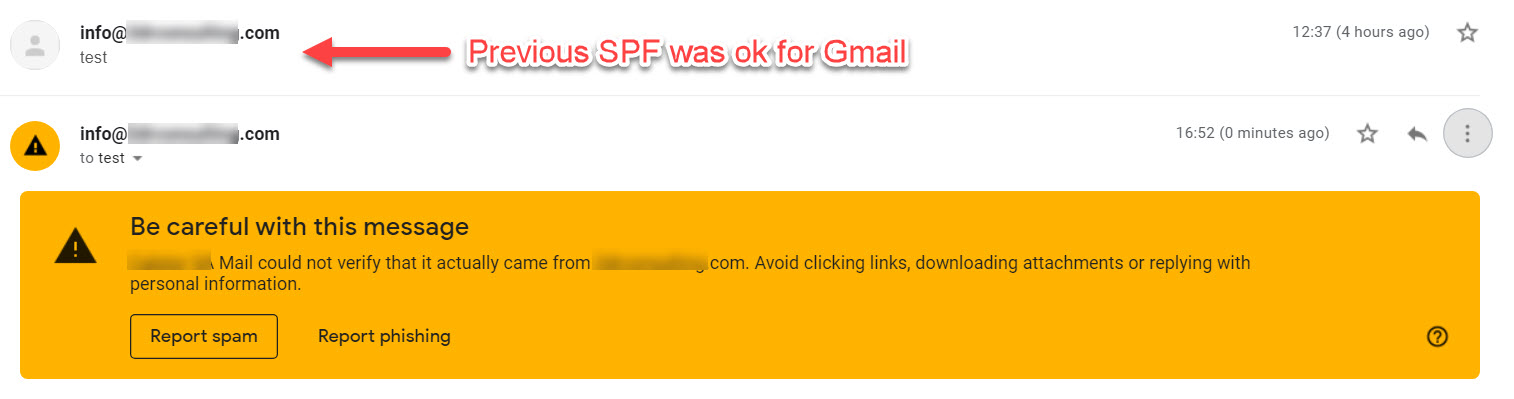
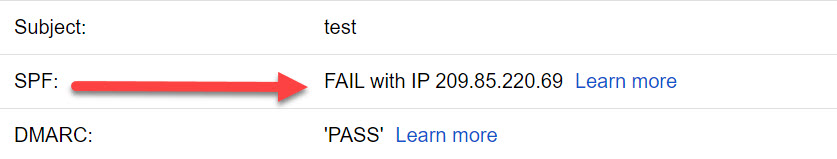
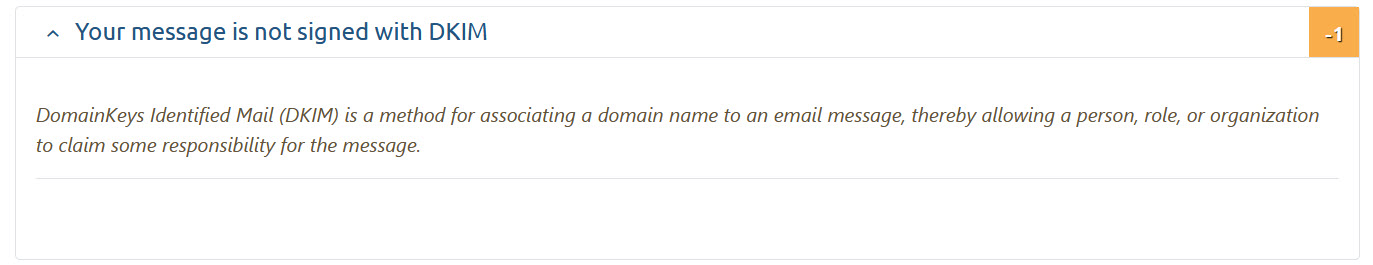
Hello!
I’ve set up DKIM following the steps in the tutorial, copied the value from Account Manager > DKIM Keys/DNS Management, removed the “” (as the domain’s on Cloudflare), however MXtoolbox is reporting “No DKIM-Signature header found”. SPF & DMARC are working correctly.
This is the Cloudflare DNS entry:
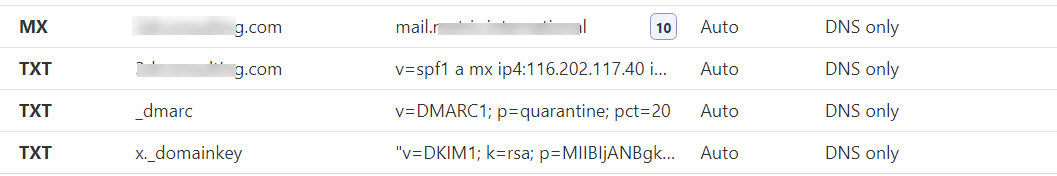
Thank you!